Last Updated on May 14, 2024 by Arnav Sharma
Azure application security groups and Azure network security groups are both powerful tools used to protect your applications and resources in Azure. Both the vital for Azure Security and easy to configure.
However, there are some critical differences between NSG and ASG that you should be aware of before deciding which one is right for you.
Application security groups are designed to protect applications, while network security groups are designed to protect networks.
Application security groups can filter traffic to and from an application, while application security groups can control traffic to and from a network. Azure network security group (NSG) filters network traffic between Azure resources in an Azure virtual network. NSGs or network security can be associated with either a network interface, virtual machine interface, or subnet/subnets.
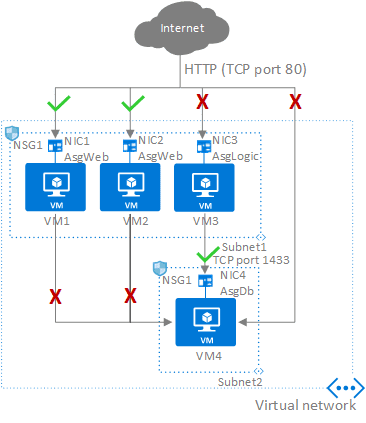
Application Security Groups (ASG) are a feature within Azure that helps simplify the management of Network Security Group (NSG) rules. ASGs can be used to group related applications together and manage their security together.
For example, you could create an ASG for all your web applications and another ASG for all your database applications. You can then add NSG rules to the ASGs that apply to all the applications within that group. This makes it easy to manage the security for all your applications at once.

ASGs can also be nested within other ASGs. This allows you to create a more granular level of security for your applications. For example, you could have an ASG for all your web applications and then create a sub-group within that ASG for all your high-security web applications.
- All network interfaces assigned to an application security group must belong to the same virtual network as the first network interface assigned to the application security group is in.
- If you specify an Application Security Group (ASG) as the source and destination in a security rule, Network Interfaces in both ASGs must exist in the same Virtual Network.
To adequately mitigate security risks, you should designate security groups according to their function instead of using individual IP addresses or ranges of IP addresses.
Azure Firewall vs NSG: Two different security solutions from Microsoft.
Microsoft offers two different security solutions for Azure: Azure Firewall and NSG. Both of these solutions have advantages and disadvantages, so choosing the right one for your needs is essential.
Azure Firewall is a managed firewall service that protects your Azure resources. It is a cloud-based solution that is easy to deploy and manage. Its has a variety of features, like SSL inspection, and inbound and outbound traffic filtering, allow or deny traffic based on a large number of factors.
NSG is a network security group that can be used to control traffic in and out of your Azure resources. It is less scalable than Azure Firewall and provides limited features, but it is easy to deploy and manage.
Q: What are Azure Application Security Groups (ASGs)?
A: Azure Application Security Groups (ASGs) allow you to group virtual machines and define network security policies based on those groups.
Q: How are ASGs different from Network Security Group (NSG)?
A: An NSG is associated with a subnet and helps control network traffic by defining security rules. ASGs are used to simplify the process of defining these security rules by allowing you to group virtual machines together and apply rules to those groups instead of manual maintenance of explicit IP addresses.
Q: What is a Network Security Group (NSG)?
A: A Network Security Group (NSG) is a container for a set of security rules that enable you to filter network traffic based on ports, protocols, and source/destination IP addresses. NSGs are associated with subnets in a virtual network and can be applied to individual virtual machines or a set of virtual machines.
Q: Why do we need security groups in Azure?
A: Security groups enable you to configure and control network traffic flow. This is a critical aspect of cloud security since a compromised workload can affect the entire network. By using security groups, you can limit the impact of an attack or security vulnerability.
Q: What is the default security rule in an NSG?
A: By default, an NSG blocks all inbound traffic coming to a subnet/virtual network interface associated with it, but all outbound traffic is allowed.
Q: How is network security policies based on these groups using ASGs?
A: With ASGs, you can define network security policies based on the application and service needs. You can determine the types of traffic allowed in and out of a particular group of virtual machines. In Azure, ASGs are used to simplify the ruleset creation for large number of virtual machines.
Q: How does a single NSG work?
A: A single NSG can be applied to multiple subnets or virtual machines, and the same security policy will be applied to all of them. This is useful if you have multiple virtual networks with a similar security posture, or if you want to apply a security rule to a specific group of virtual machines.
Q: What is the difference between Network Security Group (NSG) and Application Security Group (ASG)?
A: The main difference between an NSG and an ASG is that an NSG is associated with a subnet, while an ASG is associated with a group of virtual machines. ASGs enable you to apply rules to a group of machines, while NSGs are used to control network traffic to and from subnets.
Q: What does manual maintenance of explicit IP addresses mean?
A: In the absence of ASGs, you may have to maintain a list of explicit IP addresses for each virtual machine in your network security ruleset. This can become challenging as the number of virtual machines increases.
Q: How do I use Azure Application Security Groups?
A: To use Azure Application Security Groups, you first need to create and configure ASGs in your Azure portal. Once created, you can assign virtual machines to a specific ASG and then assign security policies to that group.